processpark
IT Security Audit Checklist xls - Ready to Download
IT Security Audit Checklist xls - Ready to Download
Couldn't load pickup availability
IT Security Audit Checklist XLS - Ready to Download
What is IT security ?
The objective of IT security management is to establish and implement security controls that align with the organization's risk appetite, ensuring the protection of digital information and the IT systems that store, process, and transmit it. IT security requirements are based on business, technical and regulatory requirements which can be combined as internal and external factors.
IT security checklist template
The scope of IT security checklist is as follows :
- IT security governance
- Identity and access management
- Protect against malware
- Managing security technology
- Manage endpoint security
- Manage network and connectivity security
- Monitor the infrastructure for security related events
- Application security
- Service design
- Security of cloud services
- Manage physical access to IT assets
- Securing AI systems
The content helps you prepare for an security audit as well as identify areas for improvement. You may also utilize the security checklist for internal control purposes. A COBIT based structured approach is adopted, focusing on IT security risks addressed through 74 questions (topics) which are supported by descriptions. You can also use the Excel-format security checklist to plan and manage actions based on your audit result.
If you have any questions related to this security checklist, we will be happy to answer these within 48 hours.
You may find this article useful where we list our findings of a real-life IT Security audit.
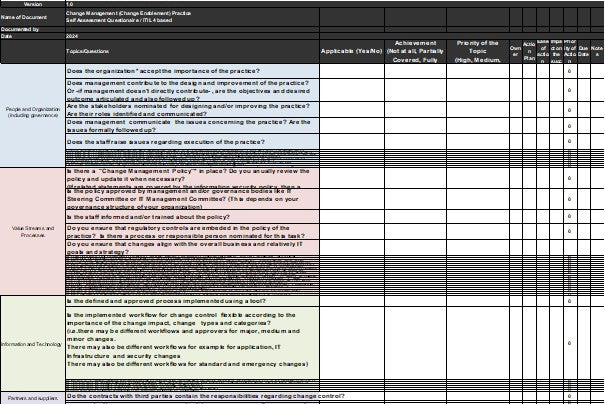
A robust change management process is a key element for IT security. Here is a change management checklist to audit or assess your process.
Here is a Third-party risk management policy to support your change management process.
Share